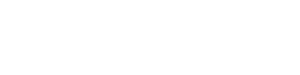Auditelcom
Auditelcom is a SaaS platform for managing fixed telephony usage. It allows you to control the use of your phones and to prevent the risks of phreaking attacks.
Usage control
For an organization, the telephone remains one of the first means of contact with its customers and suppliers. The quality of this first exchange is very important for its image and the first impression it will leave on its correspondent.
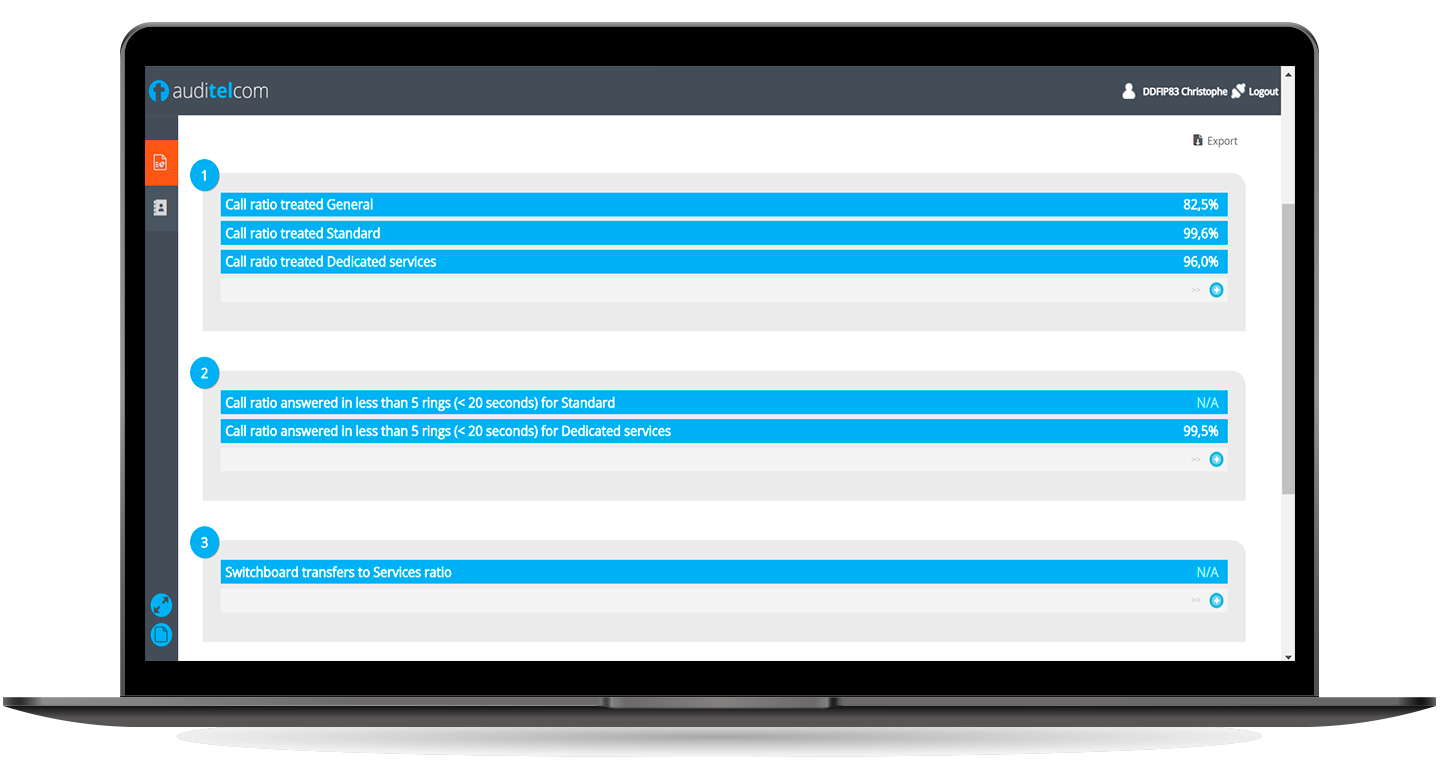
To improve its reception, it is necessary to have at least objective and reliable data concerning the analysis of the incoming traffic and in particular:
- the number of calls received
- the number of lost calls
- the time slots during which calls are lost
- the stations that lose the most calls
- waiting times
- conversation times
- etc…
With such statistics, the reception manager is able to take the appropriate measures to the situation by adding staff, modifying the operating hours, implementing alternative technical solutions, in short, by setting up an improvement plan that he can then follow from dashboards and reports.
Analysis and Alerts
A large number of companies have already suffered from phreaking attacks. These attacks consist in fraudulently breaking into your telephone system to modify certain parameters and to send traffic to exotic and expensive destinations at your expense.
Depending on the size of your installation and the length of time the attack continues without intervention, the additional cost generated by these calls can reach several tens of thousands of dollars.
CIOs can put in place a few simple management rules but also equip themselves with control tools adapted to the detection of such offences such as AUDITELcom.
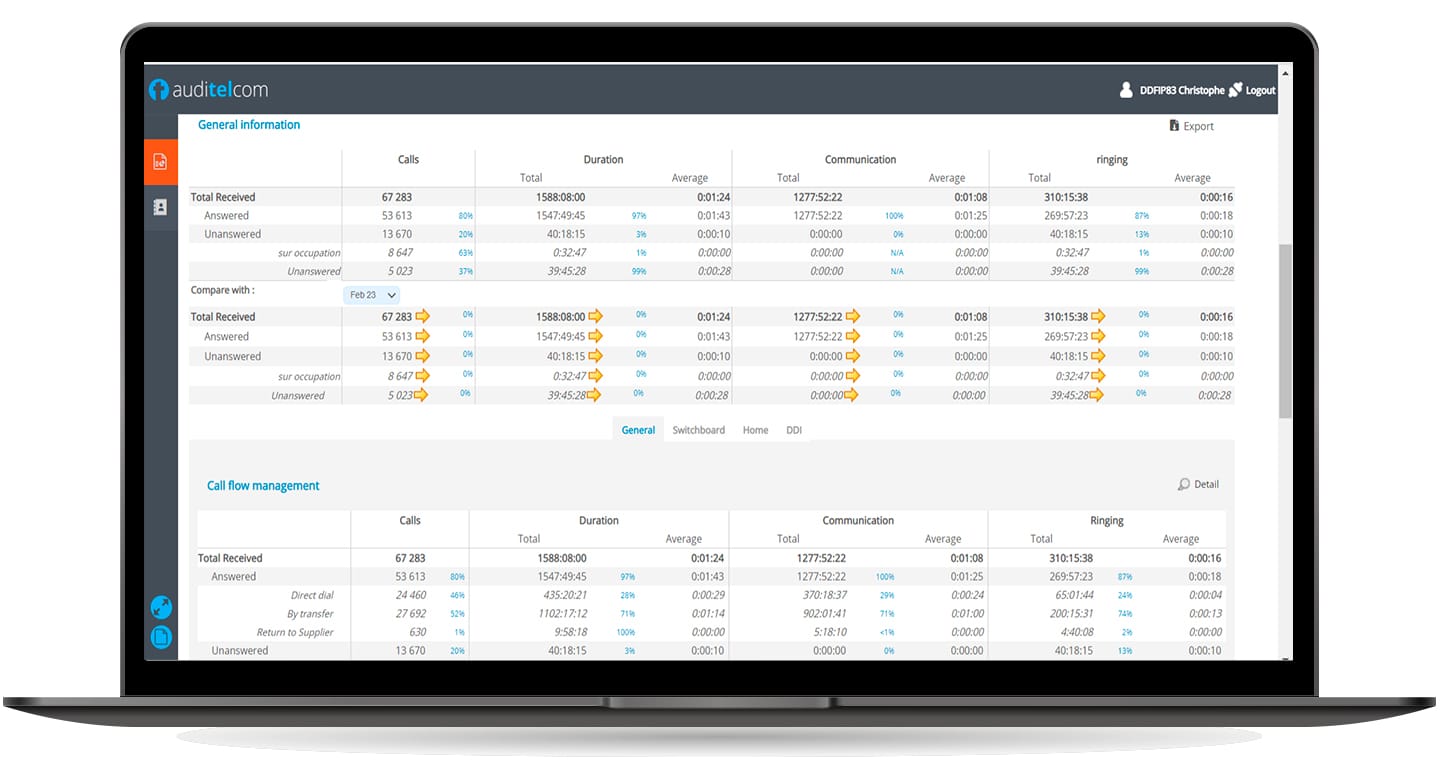
Based on the real-time analysis of the call traces emitted by your installation, you have monitoring and alerting solutions. You can then identify, as soon as an attack begins, a large number of calls or unusual call destinations.
Depending on defined thresholds, one or more people are notified in real time and can intervene on your installation to restrict or cut off communications, thus limiting the financial loss generated by this type of attack.